In this section you can manage your account’s security settings. We encourage you to enable Two-Factor Authentication and review the other settings in order to keep your account secure.
For additional notes about Two-Factor Authentication and Application Passwords we recommend you read the page More About Two-Factor Authentication and App Passwords once you have read this overview.
Contents
Two-Factor Authentication
Two-Factor Authentication (2FA) refers to a log in procedure where there is an additional piece of information required in addition to the usual username and password. This additional piece of information is usually something that can only be used once, or for a limited period of time, and then a new different piece of information is required.
Important Note:
When you activate 2FA your usual account password will no longer work for IMAP, POP, SMTP, FTP and Cal/CardDAV services. This means you will need to use Application Passwords (see below) for all email, calendar, address book and FTP apps/programs you are using. You will still be able to access your email using our webmail service.
When Two-Factor Authentication (2FA) is enabled, you will have the following options:
Timed One-Time Passwords (TOTP)
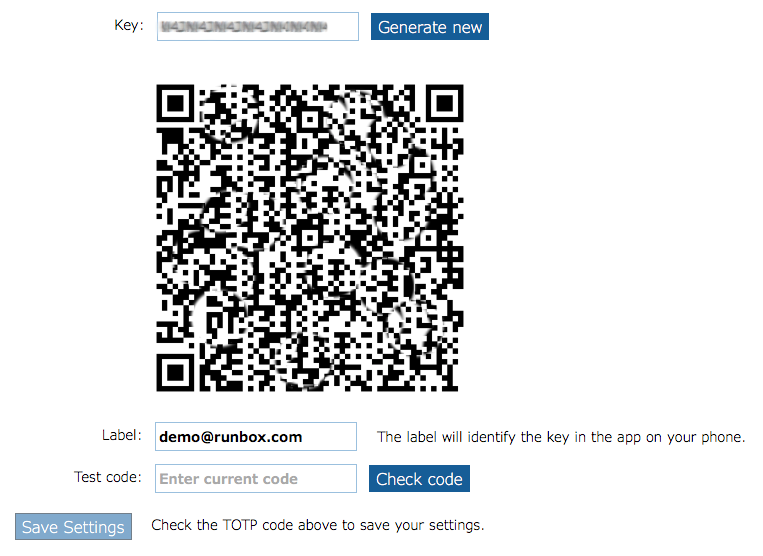 To use this option you will need a smartphone and some free software.
To use this option you will need a smartphone and some free software.
Timed one-time passwords works by giving you a login code which changes over time, in addition to your password.
To get started, download a TOTP app such as Authy, FreeOTP or Google Authenticator onto your mobile phone and follow their instructions.
Note: It is essential that your smartphone has the correct date/time set as this is used by the TOTP app to generate the correct codes that allow you to log in.
One-Time Passwords (OTP)
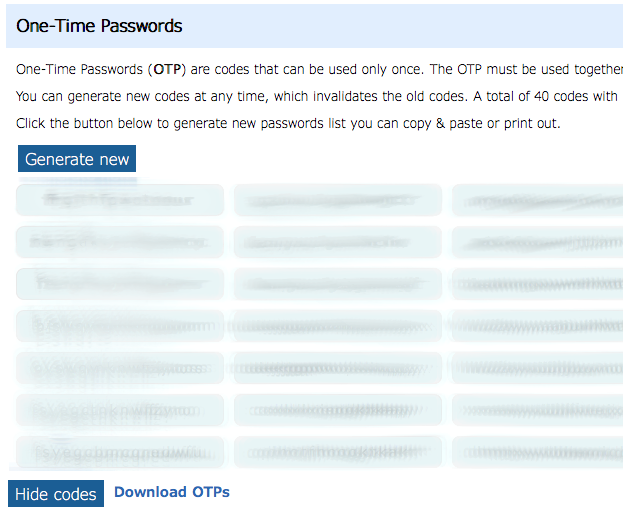 When you enable this option, the system will generate random passwords that you can use only once. Used passwords are discarded automatically and cannot be used again.
When you enable this option, the system will generate random passwords that you can use only once. Used passwords are discarded automatically and cannot be used again.
You can download the the list of passwords to a computer or mobile device, or you can print them out if necessary. However, you must keep the list secure as these passwords can be used to access your account along with your usual username and account password.
Trusted browsers
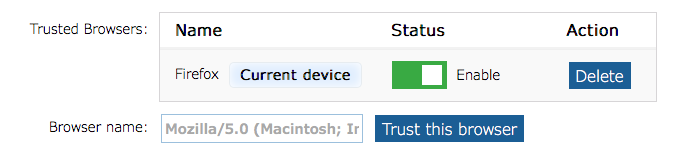 This option allows the server to trust your current web browser so that you don’t have to use a 2FA code. The option places a small piece of code in your browser (a cookie) that tells the server not to require the 2FA details and you can just log in with username and password.
This option allows the server to trust your current web browser so that you don’t have to use a 2FA code. The option places a small piece of code in your browser (a cookie) that tells the server not to require the 2FA details and you can just log in with username and password.
You should only use this method of bypassing 2FA on a computer or device that you are confident nobody else can log in to. You can temporarily turn on/off individual browsers from the trusted list, or you can delete the browser entry entirely which will force that browser to require the 2FA details.
Unlock code
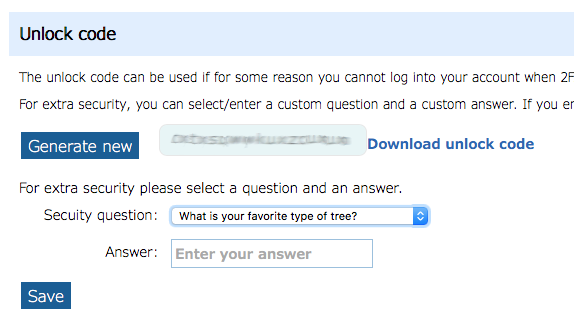 If for some reason you are unable to log in with 2FA after it has been enabled, this code can be used to disable 2FA.
If for some reason you are unable to log in with 2FA after it has been enabled, this code can be used to disable 2FA.
The code can be used in conjunction with a secure question/answer for additional security.
Manage Services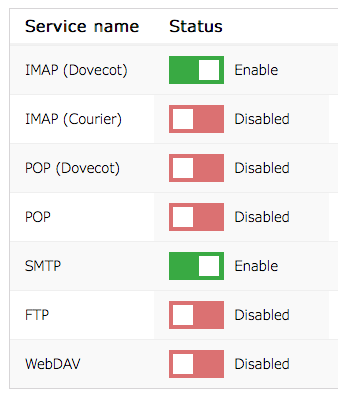
This section lets you enable and disable the various services such as IMAP, POP, and SMTP. Disabling the services you don’t use protects your account from attempts at unauthorized access on those services. For example, you might want to disable all services if you only ever use the webmail.
Disabling a service will stop it working across all devices, whereas disabling an Application Password (see below) stops that application working on all services.
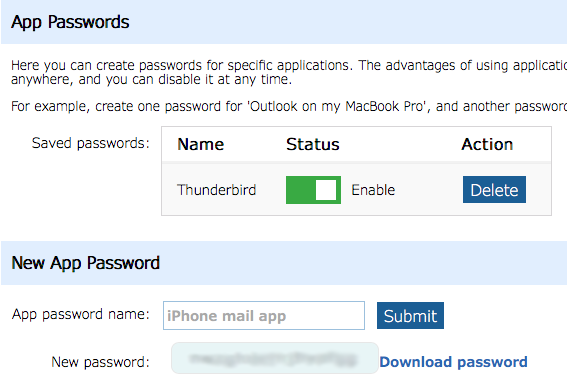
App Passwords
Application Passwords (app passwords) can be used in email programs such as Outlook, Apple Mail, and Thunderbird, and allows fine-grained control over each device’s or app’s authentication.
App passwords are not a form of Two Factor Authentication, but they are often used in conjunction with it to provide additional security for your account. They do this in a number of ways.
- If you use the webmail, and someone looks over your shoulder and sees your password, then by using different passwords for email apps etc. this will mean that they cannot use the password they saw you enter to access your account using an email app. Furthermore, as you should be using 2FA on the webmail, the password won’t work there either as they would require the current additional piece of information (a TOTP or OTP) in addition to the password.
- Keyloggers or monitored computer networks won’t be able to log enough information to access your account when logging in via webmail.
- Runbox generates the app password ensuring it is random and difficult to “guess”.
- The interface only shows you the app password once, and this encourages you to use different app passwords in different places.
 Although they are called app passwords, they are not actually specific to an individual email app, and can be used for logging in on any email app. Their value is in the fact you don’t usually type them in each time you log in using an email app. This means they cannot be discovered so easily by keyloggers or someone watching your type on your keyboard.
Although they are called app passwords, they are not actually specific to an individual email app, and can be used for logging in on any email app. Their value is in the fact you don’t usually type them in each time you log in using an email app. This means they cannot be discovered so easily by keyloggers or someone watching your type on your keyboard.
If you use app passwords specific to each device and then lose a device, you can easily disable that password and prevent that device from logging in. In this case you would be using “app passwords” more like “device passwords” and perhaps using the same password for a number of clients on that device (e.g. email, CalDAV and FTP).
If you require a more fine-grained level of control, you could use a different password on every app on the same device, and in the case of email one for incoming mail and one for outgoing mail. However, please remember that all passwords are valid for all services.
